

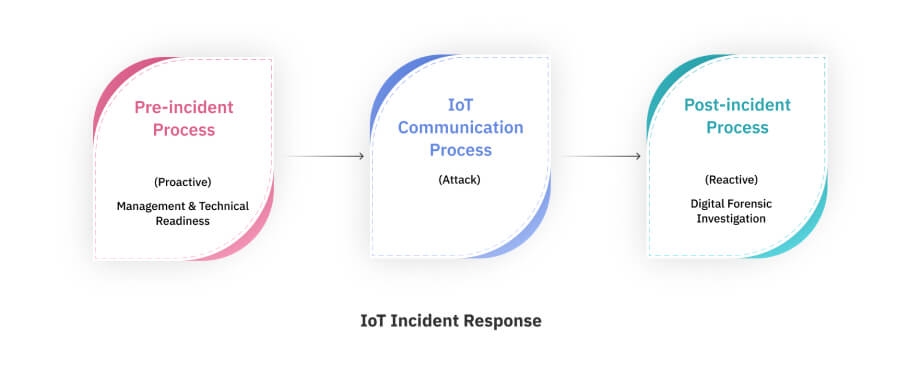
Internet of Things, or IoT, has found its application in all areas of life. IoT devices have proven to be extremely beneficial in performing a variety of tasks. In addition to this, they have proven to serve another purpose; the purpose of providing digital evidence. IoT devices are becoming digital eyewitnesses in today’s world. IoT forensics is the branch that deals with the retrieval, recovery and interpretation of the data present on the IoT devices like health trackers, home assistants, security cameras and TVs to aid in the investigation of cybercrimes. They store information about the events and operations performed by them, which can be of importance if that information is related to some criminal activity.
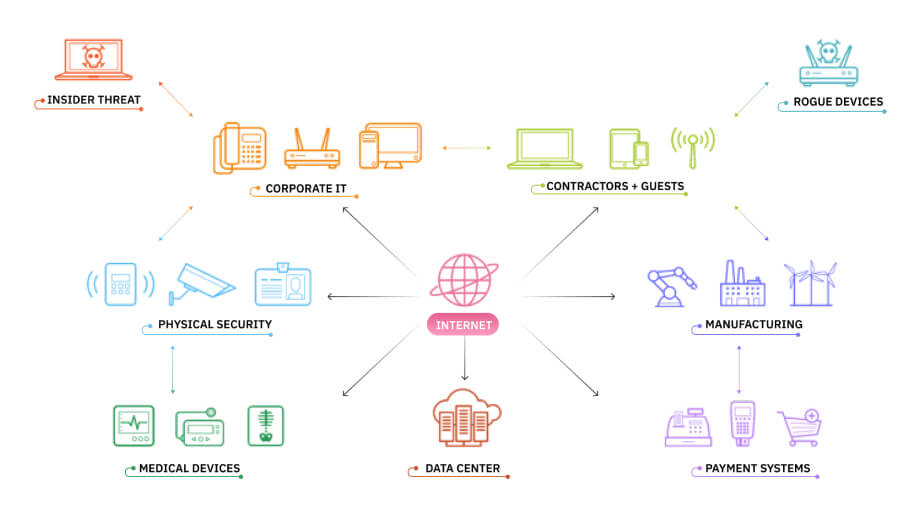
A health tracker maintains records of the number of steps taken by the user, his/her heartbeats, energy level, fitness level etc. A smart car that is connected to the internet records the locations where the car has travelled. A smart refrigerator stores the information of the food items consumed by the user. A home assistant keeps track of the search queries performed by the user. By analysing the user’s daily routine, work schedule, fitness level, hobbies, interests, browsing history and other activities, IoT devices are able to recognise the user’s traits, habits and behavioral patterns. Moreover, the devices can help build a timeline of the events that have occurred in the past. Hence, they make the criminal investigation process a lot easier.
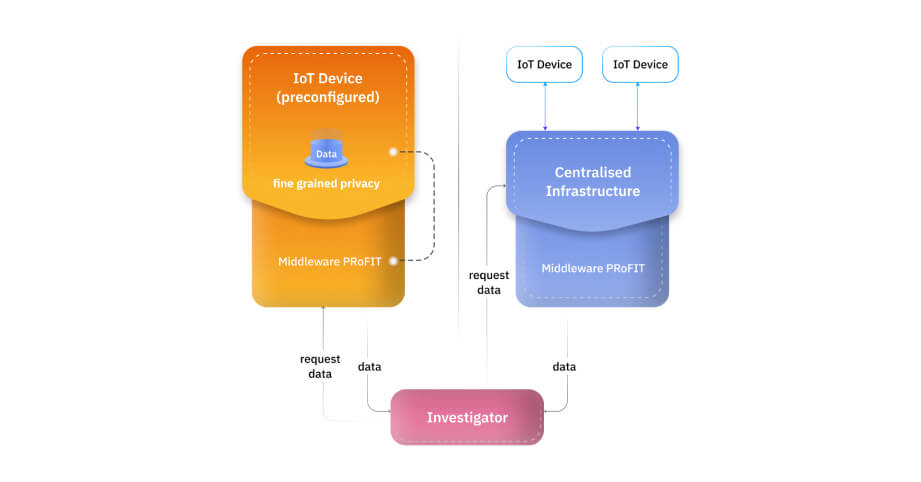
The data stored on the IoT devices, however, is not completely secure. In 2016, the largest DDoS attack was implemented using an IoT botnet which was made possible by a malware called Mirai. Many websites like Twitter, Netflix, Reddit etc went down. The infected computers searched for vulnerable IoT devices on the internet. By using default usernames and passwords, access to the devices was gained to further infect them. Implantable cardiac devices that are used to monitor the patient’s heart functions can be hacked by exploiting the vulnerabilities present in them. The hacker can deplete its battery and administer incorrect pacing. Since a hacker can destroy or modify the records stored on the IoT devices, the evidence present on them becomes unreliable. The potential of IoT devices to build an accurate timeline of events, to recognise the personality of the suspect and to qualify as digital eyewitnesses, is lost.
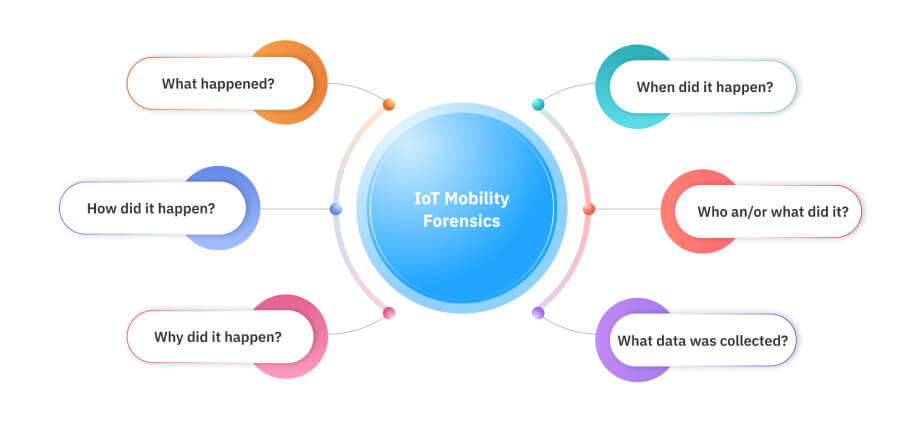
IoT devices are developed by keeping their functionality and cost into consideration. They are designed to function with minimum ancillary software. To make the devices more secure, security experts would have to perform penetration testing and additional security solutions would have to be deployed. This would lead to an increase in the cost of the device and may limit its functionality. Thus, there is a trade-off between the security of the devices and the cost and functionality of the devices.
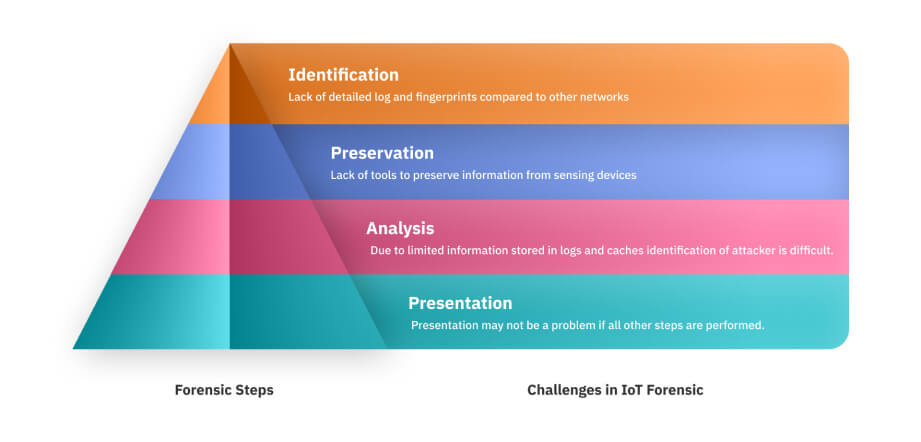
It is true that 100% security is unattainable. But, building a concrete system that performs reliable digital forensics, which consequently makes it possible to track down the actors responsible for the cybercrime, is the need of the hour. The crucial role that IoT forensics plays needs to be understood. IoT forensics can prove to be successful only when the security of IoT devices is increased.

We work with ambitious leaders who want to define the future, not hide from it. Together, we achieve extraordinary outcomes.